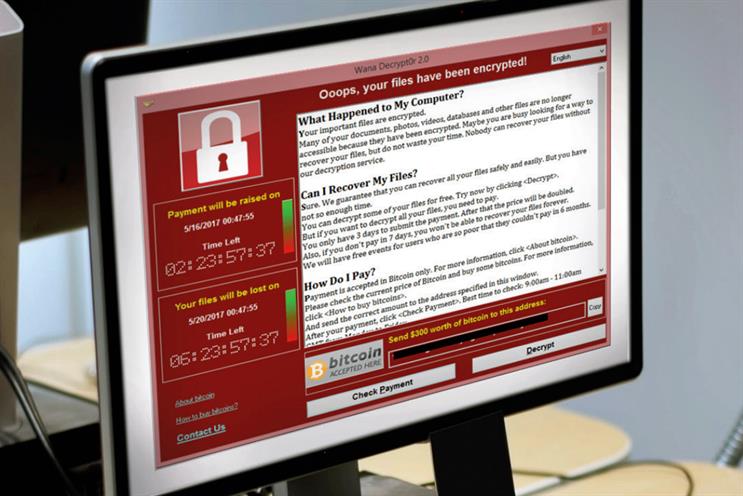
Last month, computer worm WannaCry garnered much attention as it rampaged around the digital world, crippling systems and leaving havoc wherever it landed. This particular worm falls under the category of "ransomware", wherein important documents on an affected system are made unreadable, usually through some method of encryption.
Once files have been taken hostage, the software then displays a ransom message on screen, detailing the actions required to release its prisoner.
In the case of WannaCry, the price of restoring access to documents ranged from $300 to $600, payable to an anonymous address using cryptocurrency Bitcoin.
Despite the story of WannaCry being reminiscent of a Tom Clancy plot, with its heavy references to black-hat hackers and shadowy government organisations, in reality this is a common occurrence.
Ransomware is not new and is the fastest-growing type of cyberattack in the world. Thousands of variants have already been set lose globally and the number grows daily.
The general population has been dealing with attacks of this nature since 2005 and, according to security vendor SonicWall, more than 638 million ransomware attacks were launched in 2016 – a 16,000% increase on the year before.
WannaCry did manage to take advantage of one of our fundamental weaknesses: inertia. Who is to blame for that? You.
Like most malicious software, the initial attack vector for WannaCry is hypothesised to have been contained within an email attachment, which, once opened by an unsuspecting user, quickly began to seek out other vulnerable systems across the computer network it was attached to.
This spread across networks took advantage of the well-known flaw in Microsoft networking code – famously discovered and then weaponised by the US National Security Agency in secret, until stolen and shared with the world by hacking group The Shadow Brokers. This has allowed WannaCry to spread with blinding speed.
At the time of writing, the number of affected systems is in the hundreds of thousands in more than 150 countries, and continues to grow. More nefariously, as this worm is able to infect the embedded operating systems used in manufacturing systems and even medical devices, well-known corporations and public-health services have fallen victim to the attack or have had to suspend operations to ensure they are not susceptible.
Although a speculative statement, I believe WannaCry was cobbled together by opportunistic, semi-professional hackers looking to capitalise on a well-known software exploit. The software isn’t elegant and was even temporarily halted by a resourceful security blogger, who found a bug in the code while trying to determine how far the worm had spread.
Diligence and hygiene are not the most exciting parts of the modern digital world but the consequences of ignoring them must now be clearly understood.
This was not a co-ordinated attack; it was a crude attempt to make a quick buck. However, WannaCry did manage to take advantage of one of our fundamental weaknesses: inertia. Who is to blame for that? You. This situation was largely avoidable and the solution was simple: update your software.
Patches have been available for nearly two months and Microsoft even took the extraordinary step of releasing an update for the 15-year-old Windows XP operating system once the worm began to spread.
Diligence and hygiene are not the most exciting parts of the modern digital world but the consequences of ignoring them must now be clearly understood.
Excuses of budgets, priority and immediate return on investment are simply myopic.
We expect the systems at the heart of our existence to be given the care and attention they deserve. We trust our physicians to wash their hands before they operate. We expect doors protecting valuables to be secured and keys not to be given to strangers. It’s boring but we expect it from the brands we trust. This is not the first such attack, nor will it be the last.
Now, please go and make sure your anti-virus software is up to date and your IT department is well-fed (pizza is always a good choice) and well-funded.
Scott Ross is the chief technology officer, international at DigitasLBi.